The Power of AWS KMS for Encryption and Compliance
Introduction
In today’s digital era, data privacy and security are more critical than ever. Whether you’re running a startup, managing enterprise systems, or offering services in the cloud, protecting user data should be a top priority. Within the AWS ecosystem, one of the most robust tools for managing encryption and safeguarding sensitive information is the AWS Key Management Service (KMS). In this article, we explore how AWS KMS works, why it’s essential for compliance (including GDPR), and how it provides enhanced control and transparency over your encrypted resources.
What Is AWS KMS? AWS Key Management Service (KMS) is a fully managed service that enables you to create and control the cryptographic keys used to encrypt your data. KMS integrates seamlessly with most AWS services, making it easy to apply encryption across your architecture with a centralized key management solution.
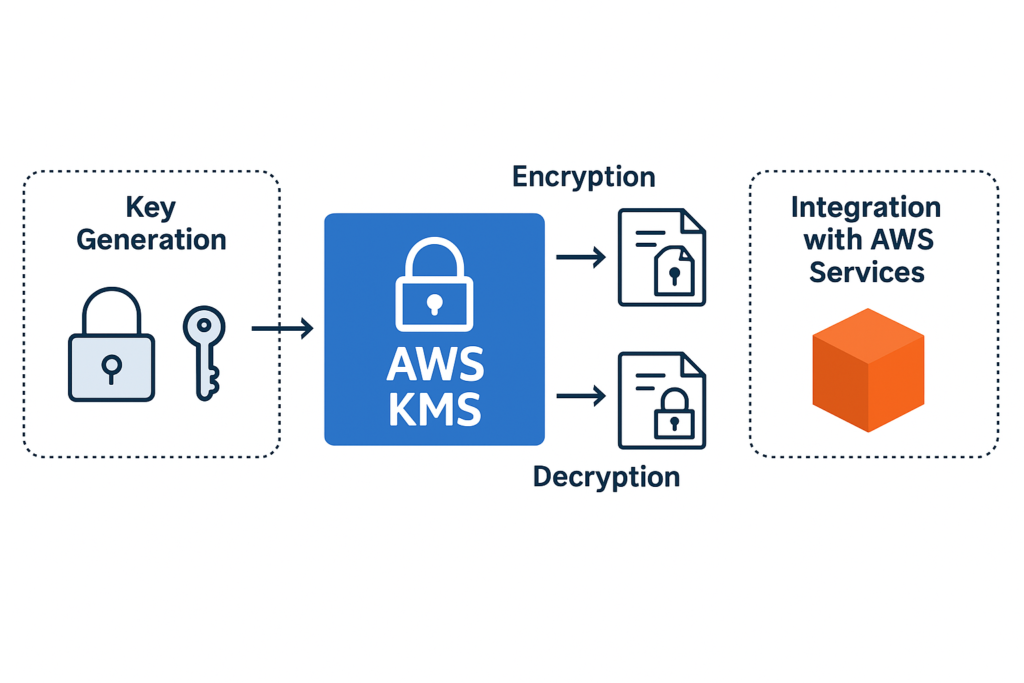
Key Features:
- Centralized key management
- Integration with AWS services (e.g., S3, EBS, RDS, Lambda)
- Fine-grained access control with IAM
- Automatic key rotation
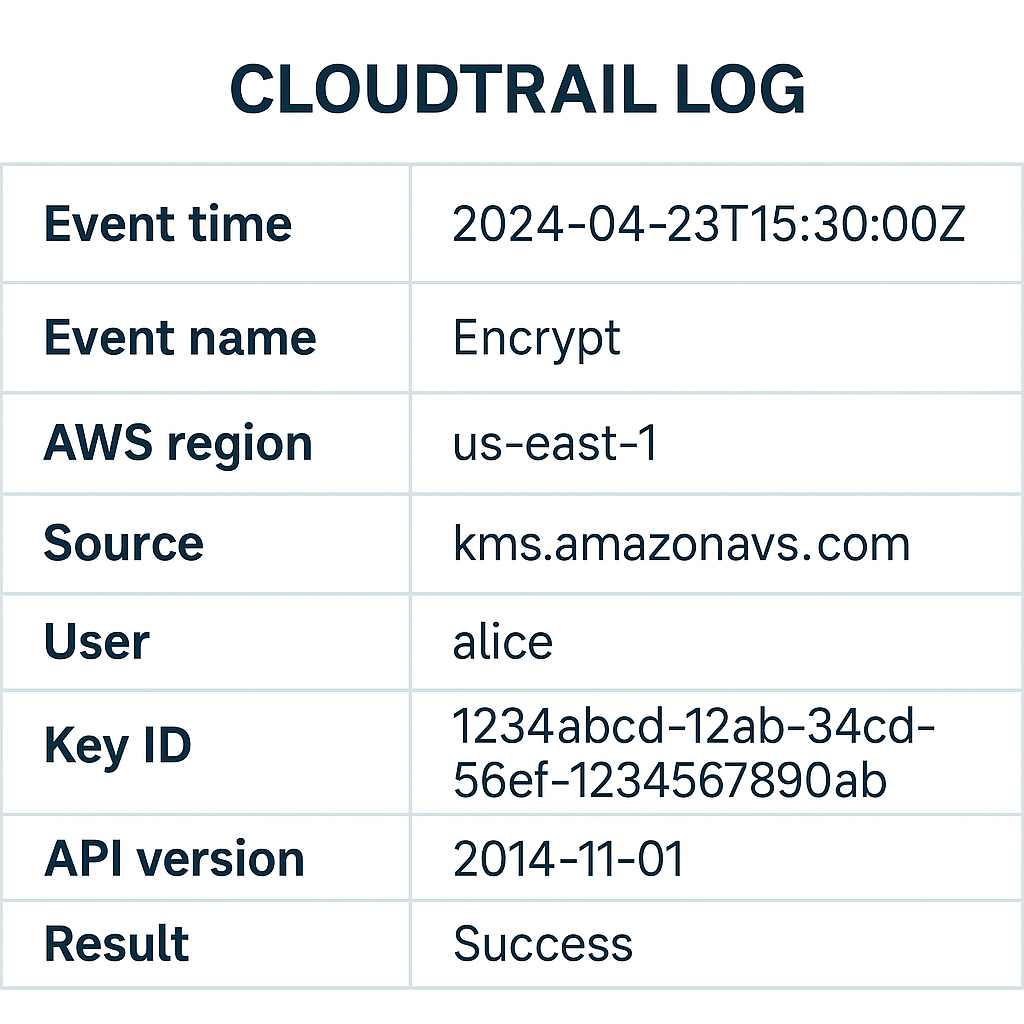
- Detailed logging through AWS CloudTrail
The Importance of Encryption for Compliance When dealing with sensitive customer data, compliance with data protection regulations such as the General Data Protection Regulation (GDPR) is not optional—it’s mandatory. GDPR, among other things, mandates:
- Data minimization and pseudonymization
- Secure processing and storage of personal data
- Ability to demonstrate security measures
Encryption is one of the most effective ways to meet these standards. By using KMS, you ensure that your encryption keys are stored and managed securely, with full visibility into how and when those keys are used.
Use Case: Encrypting Data in Amazon S3 with KMS Amazon S3 offers built-in encryption features, including SSE-S3, SSE-C, and SSE-KMS. While SSE-S3 encrypts data at rest automatically, it uses Amazon-managed keys. SSE-KMS, on the other hand, uses keys stored in AWS KMS, offering additional benefits:
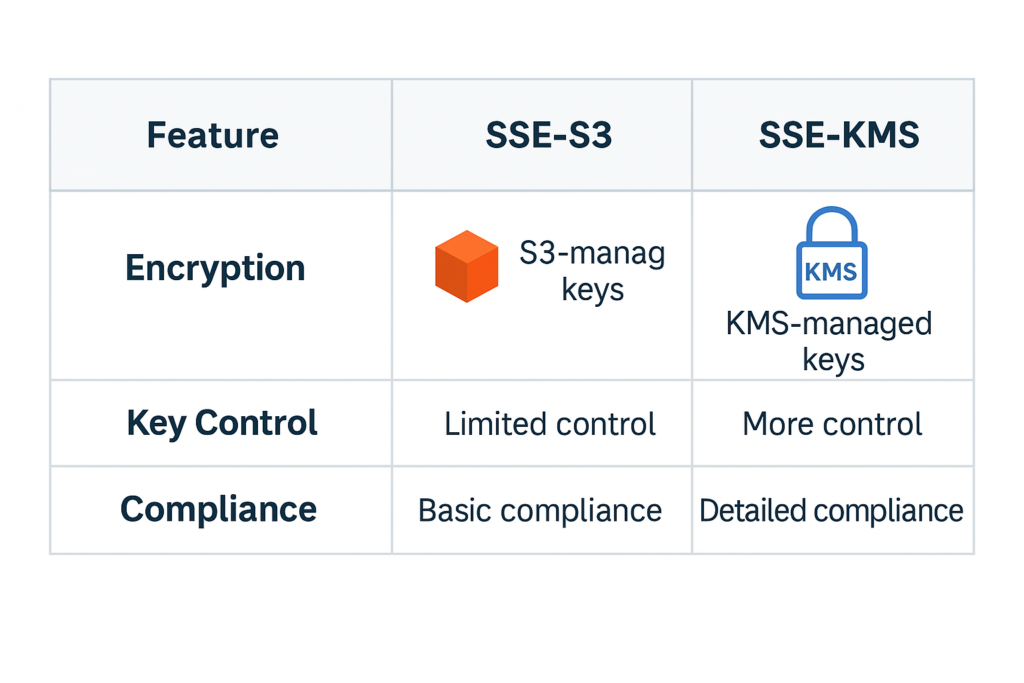
Advantages of Using KMS with S3:
- Granular Access Control: Define who can use specific encryption keys using IAM and key policies.
- Audit Logging: Track every access and action taken on your encryption keys using AWS CloudTrail.
- Customer-Managed Keys: You can create, rotate, disable, and revoke your own Customer Master Keys (CMKs).
- Compliance Support: Demonstrate encryption and key usage to auditors with detailed logs.
Example Scenario: Imagine you’re storing user-uploaded documents in an S3 bucket. With SSE-S3, your data is encrypted, but you lack fine-grained control and visibility. By switching to SSE-KMS, you:
- Assign a unique CMK for each business application.
- Control which roles or users can decrypt which files.
- Log and analyze decryption attempts to detect anomalies.
Security is a Shared Responsibility One of the key principles of AWS is the Shared Responsibility Model. While AWS secures the infrastructure, it is up to the customer to configure and manage their security controls, including data encryption. Tools like KMS empower you to uphold your end of this model with confidence and precision.
Best Practices for Using AWS KMS
- Enable key rotation for long-term security
- Use IAM policies and grants wisely to avoid overly broad access
- Regularly review your CloudTrail logs for suspicious activity
- Apply least privilege principles to KMS usage
- Store audit logs in a separate, secured account or region
Conclusion Encryption is not just a technical necessity—it’s a strategic imperative. With AWS KMS, you gain a powerful, flexible, and compliant solution for managing your encryption keys. Especially when integrated with services like S3, it offers unmatched transparency, control, and accountability. As businesses grow and data regulations evolve, leveraging KMS becomes not just beneficial, but essential.
Keywords: AWS KMS, Encryption, AWS Security, GDPR Compliance, Data Protection, S3 Encryption, SSE-KMS, CloudTrail, IAM, Key Rotation, Shared Responsibility Model
This sectionReady to strengthen your data protection strategy?
Learn how to implement KMS in your current AWS workloads or contact us for a consultation on AWS security best practices.





